What is a Man-in-the-Middle (MITM) Attack:
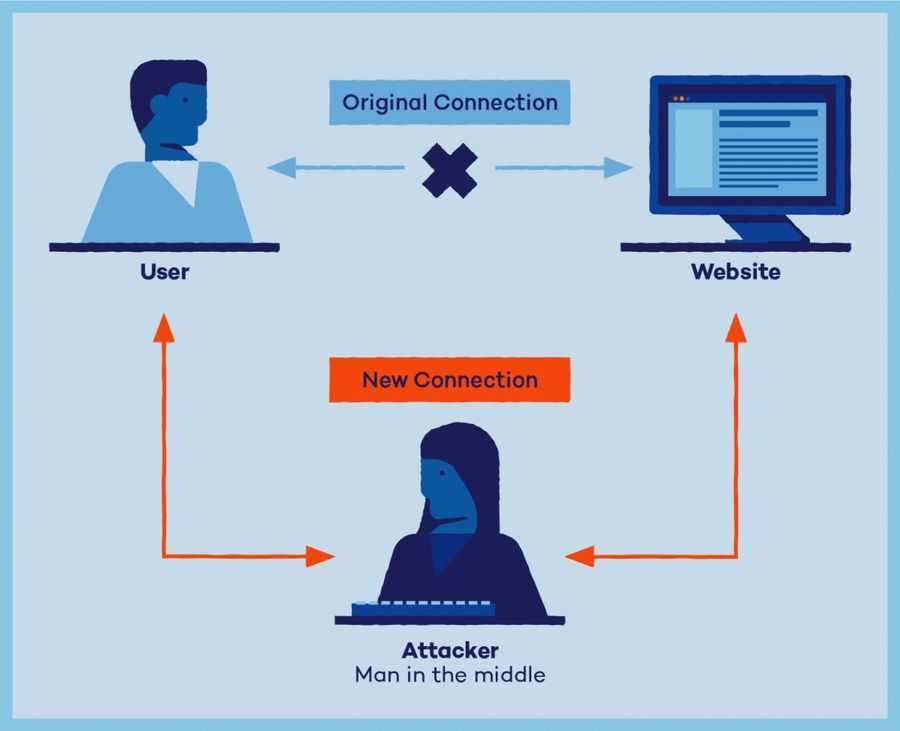
A man-in-the-middle (MITM) attack is a cyber attack where an attacker places themselves between two communicating parties, relaying messages for them, while the parties believe they are communicating directly and securely. The attacker can then monitor and possibly change the contents of messages.
MITM attacks can occur in any form of online communication, such as email exchanges, web browsing, and any other data transfer. They can be dangerous because the user may not realize that their data is being rerouted to a malicious party. MITM attacks pose serious threats to both individuals and organizations, leading to financial loss, data breaches, reputational damage, and even legal implications if sensitive customer data is compromised.
Some examples of MITM attacks include:
IP spoofing: Altering the Internet Protocol (IP) address of a website, email address, or device
HTTPS spoofing: Secretly redirecting a user to a non-secure HTTP website
Domain Name System spoofing: Cybercriminals alter domain names to redirect traffic to fake websites
Here's an analogy to illustrate how an attacker can use MITM: Janete and Marc are having a conversation; Daniel wants to eavesdrop on the conversation but also remain transparent. Daniel could tell Janete that he was Marc and tell Marc that he was Janete. This would lead Janete to believe she's speaking to Marc, while actually revealing her part of the conversation to Daniel.


 and Install Application/Add to home screen
and Install Application/Add to home screen